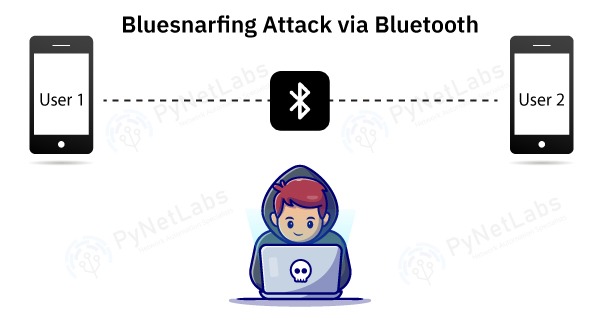
Different Bluetooth Hacking Techniques That You Should Know To Prevent Loss Of Data | Cyware Alerts - Hacker News

Avoiding WiFi and Bluetooth Hackers in Your Home | Business and Home Security Solutions | Northeast OhioAvoiding WiFi and Bluetooth Hackers in Your Home